A short while ago Mailsploit released their list of email clients they tested for vulnerability to Spoofing and XSS/Code Injection. eM Client ranked as unaffected by these mail sploits but some users were not sure about the outcome when they tested the behavior themselves, so we’d like to address it.
Our default setting in Menu>Tools>Settings>Mail>Read is to show Display name only. Display name can be set to anything, but spoofing tries to replace the actual email address in this view. So when you scroll over the address you see the REAL address, even though the Display name is set to seem like a different one.
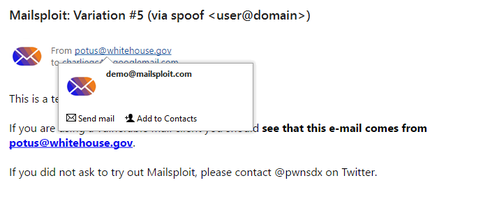
You can enable the option to ‘Show email address in email header’ in the Read settings to ensure you ALWAYS see the real address right away behind the Display name, as shown in the image below:
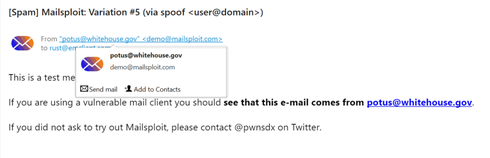
Since we ranked as unaffected, this means that other programs will not be able to show you the real address at all (not even with mouseover or even in message source in some cases).
Either way, we’d like to improve the default behavior, so we’re currently working on a feature which will show the real email address after the Display name if the Display name contains a string which is made to look like an email address, regardless of the user’s header settings.